As we have discussed previously, a strong foundation of digital identity forms the basis for effective accountability in distributed systems. We also made the case that accountability is necessary to bridge the potential of blockchain and distributed ledger technology to the needs of assets in licensed markets, i.e. “real world” assets.
In this article, I will discuss verifiable credentials as a model for digital identity. Verifiable credentials are cryptographically signed pieces of digital information that can be used to represent the information found in physical credentials such as passports, driver’s licences, and national identity documents (or any other arbitrary credential) in the digital world. These credentials, when aggregated, begin to form a picture of an individual’s digital identity online.
Most models of verifiable credentials adhere to the W3C standard, which aims to define a specific, standardised data model that can be used for interoperable digital identity.
How do verifiable credentials work?
There are three key entities with important roles in a verifiable credential data model for digital identity:
- Issuer - the entity issuing the credential
- Holder - the entity holding the credential and whose information is contained therein
- Verifier - the entity looking to verify the legitimacy of the credential
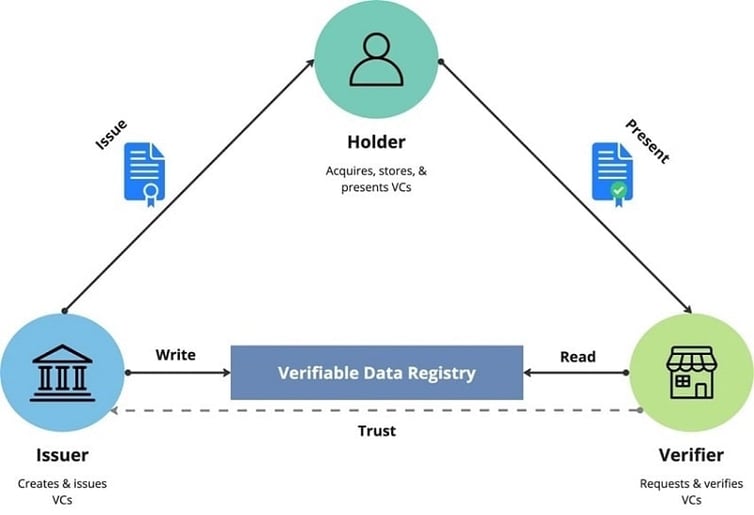
At a high level, the Issuer will typically create the credential containing the relevant personal information about the Holder, sign it using a cryptographic key, and issue the credential directly to the Holder. The Issuer will also often write some data to a verifiable data registry that can serve as an independent mediator of identifiers, verifiable credential schemas, revocation registries, issuer public keys, etc. Often more than one type of verifiable data registry is used in such a digital identity ecosystem.
Verifiers, such as businesses, can then request Holders to provide some data relating to their digital identity. For example, a business can request proof that the Holder meets specific eligibility criteria for the business’s product or service. The Holder can generate verifiable presentations and share them with the Verifier to make claims - i.e. to prove they possess verifiable credentials within their broader digital identity with specific characteristics.
The Verifier can then use the contents of the verifiable credentials, along with referencing the verifiable data registry (if required), to independently verify the authenticity and integrity of the claim about the Holder’s digital identity.
The Benefits and Potential of Verifiable Credentials
Verifiable credentials provide many benefits over and above their physical counterparts. Firstly, verifiable credentials utilise cryptographic signature schemes, which often make them more trustworthy and tamper-evident than physical documents.
Secondly, because of their digital nature, verifiable credentials and verifiable presentations can be sent and received extremely quickly and easily across the internet. This makes them much more convenient, flexible, and dynamic than their physical counterparts, enabling better user experiences when trying to establish trust between counterparties at a distance.
With a strong foundation of being able to securely, flexibly, and dynamically share the information previously confined to physical documents in convenient ways, verifiable credential-based models of digital identity have the potential to revolutionise the way we handle personal data.
In these models, the credentials sit with the Holder in a decentralised fashion, and, depending on the specifics of the implementation, can dramatically improve the degree of control, ownership, and agency of the data that makes up our digital identity.
Furthermore, these models can dramatically reduce cost, inefficiency, and risk associated with businesses having to identify individuals and other businesses. The user’s digital identity can be used over and over again instead of needing to conduct repeated manual and costly point-in-time checks to verify the validity of a particular document when, for example, a user signs up for a new product or service.

Drawbacks of Verifiable Credential Data Models
Despite these advantages, there are drawbacks to models of digital identity built on the use of verifiable credentials. The same characteristics that make verifiable credentials convenient, flexible, as well as dynamic, create challenges in a digital identity context, specifically related to privacy.
As the W3C outline,
“The persistence of digital information, and the ease with which disparate sources of digital data can be collected and correlated, comprise a privacy concern that the use of verifiable and easily machine-readable credentials threatens to make worse.”
Despite these challenges, advances in privacy enhancing-technologies such as zero knowledge-proofs and other novel cryptographic signature schemes are proving to be a promising means to tackle some of these challenges with verifiable credentials and digital identity.
Additionally, it is important to note that just because a given credential is verifiable, it does not guarantee the veracity or truth of the contents of that credential. There exists a significant trust vector between the Verifier and the Issuer. Notably, this trust vector is also present in the current analogue system of physical credentials and is a prerequisite for any future verifiable credential-based digital identity alternative.
There is a world of possibility when it comes to combining a verifiable credentials-based digital identity data layer with a secure, scalable, and accountable blockchain such as Redbelly Network. In future articles, we will dive deeper into Redbelly Network’s verifiable credential based digital identity layer and explain how it can be used to solve problems of cost, inefficiency, and risk in our economy.
About the Author: Matt is the Head of Product at Redbelly Network. He is passionate about leveraging distributed ledger technologies to scale the impact of solutions to solve super wicked problems. Matt has been working in startups and product management for more than 7 years turning product ideas into reality. He has a background in physics, philosophy, climate science and renewable energy.